Adding A System

In this section, will cover how to add a system in the Compliance / Cyber section of the In A Box platform. This process is to be performed for each unique system that requires documentation.
Table of contents
Add Systems
Similar to the Organization section, the System section is where users can define the systems that require documentation. Users will be creating a knowledge base of the systems that exist under the organization.
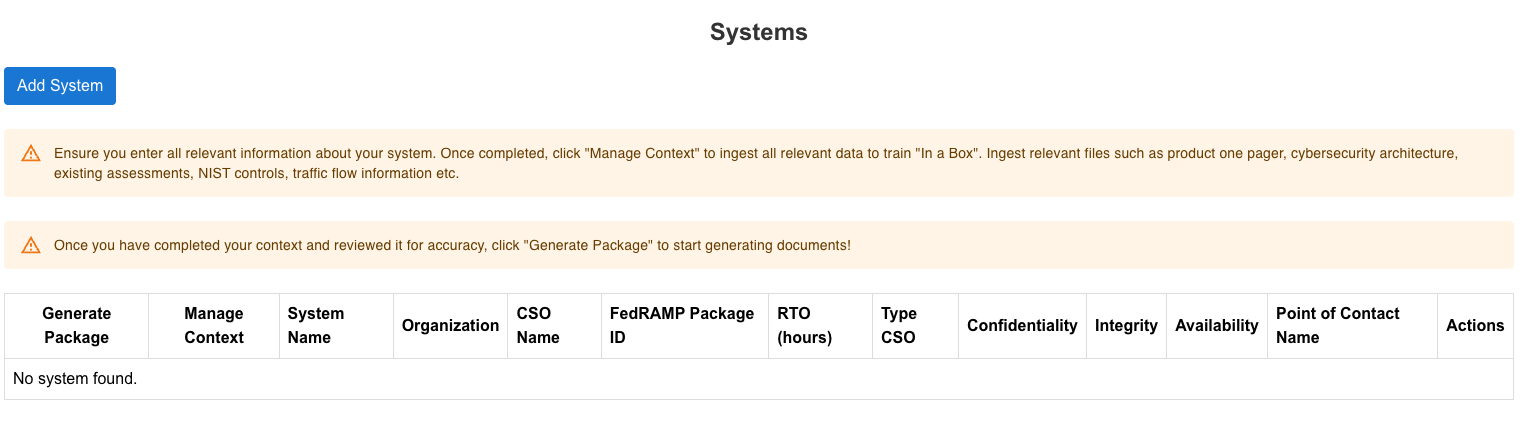
Navigate to the Compliance / Cyber section select the Systems & Packages and click on Add Systems button.
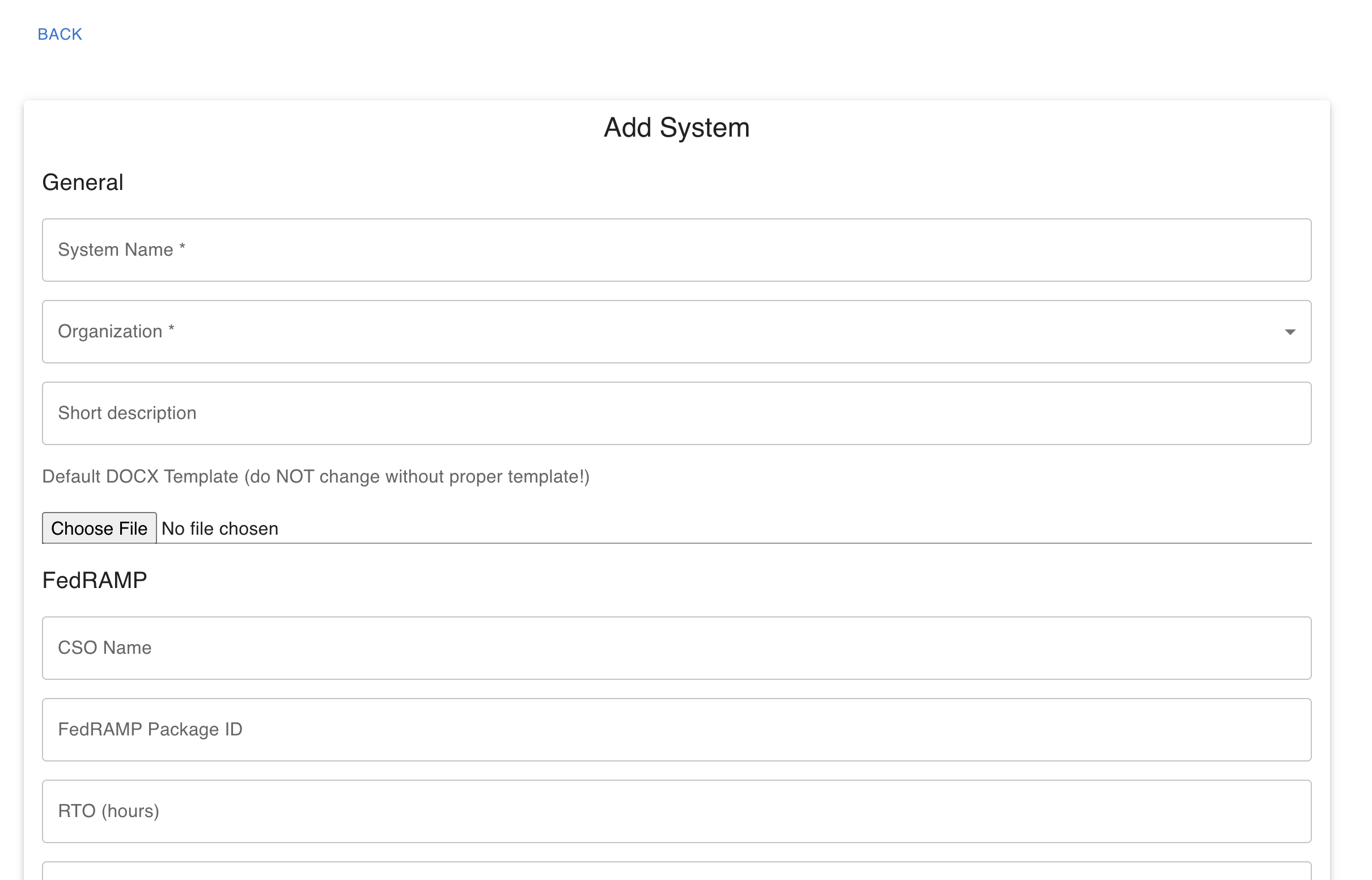
- Fill in the details for the system - some of the fields are mandatory.
- Click on ‘Add System’ to save the details.
After adding the system, users will see it listed on the Systems & Packages page. Users can add multiple systems.
Edit System
After a system is created, users can edit the system details by clicking on the Edit button under the Actions column.
Delete System
Users can delete a system by clicking on the Delete button under the Actions column for the respective system entry.
Manage Context
The Manage Context section is the main section where users are required to provide relevant information about the system. This information will be used to generate documents for the system. Relevant information includes files such as product one pager, cybersecurity architecture, existing assessments, NIST controls, traffic flow information etc.
Navigate to the Manage Context section and click on the upload button to be redirected to the first step of the Manage Context section.
Step 1. Data Collection
The data collection step is the first step in the Manage Context section. Users will be required to provide information about the system. Fill out the fields and follow the instructions to complete the data collection step. We describe this phase as the ability to consolidate all relevant unstructured data into one place.
The 5 fields in the data collection step are:
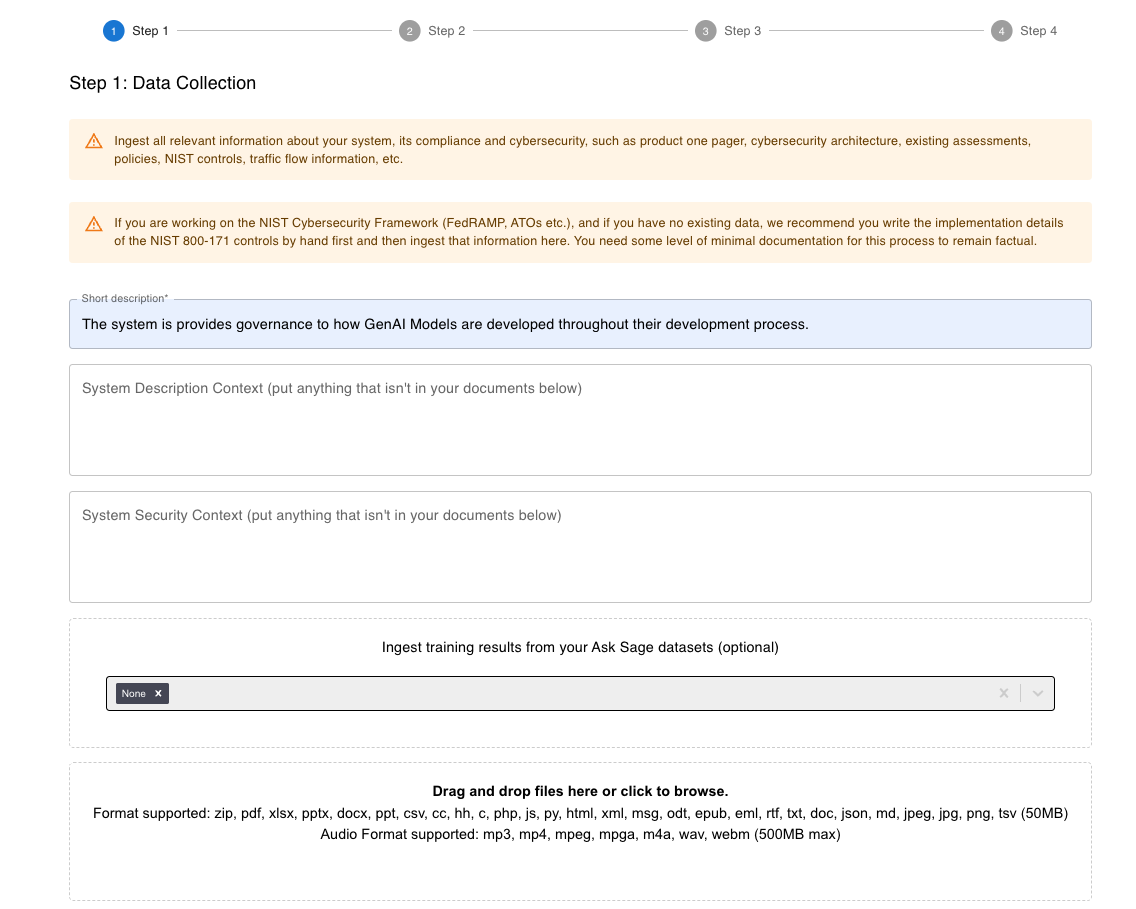
- Short Description
- Provide a short description of the system.
- System Description Context (Put anything that is not in your documents below)
- Provide any context that is not in the documents/datasets.
- System Security Context (Put anything that is not in your documents below)
- Provide any security context that is not in the documents/datasets.
- Ingest training results from your Ask Sage datasets (optional)
- Ingest training results from your
Ask Sagedataset. If you useAsk Sage, you can select datasets that are relevant to the system.
- Ingest training results from your
- Drag and drop files here or click to browse.
- Upload relevant files that are not in the datasets.
Once the data collection step is completed, click on the Next button to proceed to the next step.
Step 2. Data Collected Review
The data collected review step is the second step in the Manage Context section. All of the data/information provided in the data collected review step will be consolidated and displayed in this step. Followed by a prompt that is then used to prompt Ask Sage to review the data/information provided in this step.
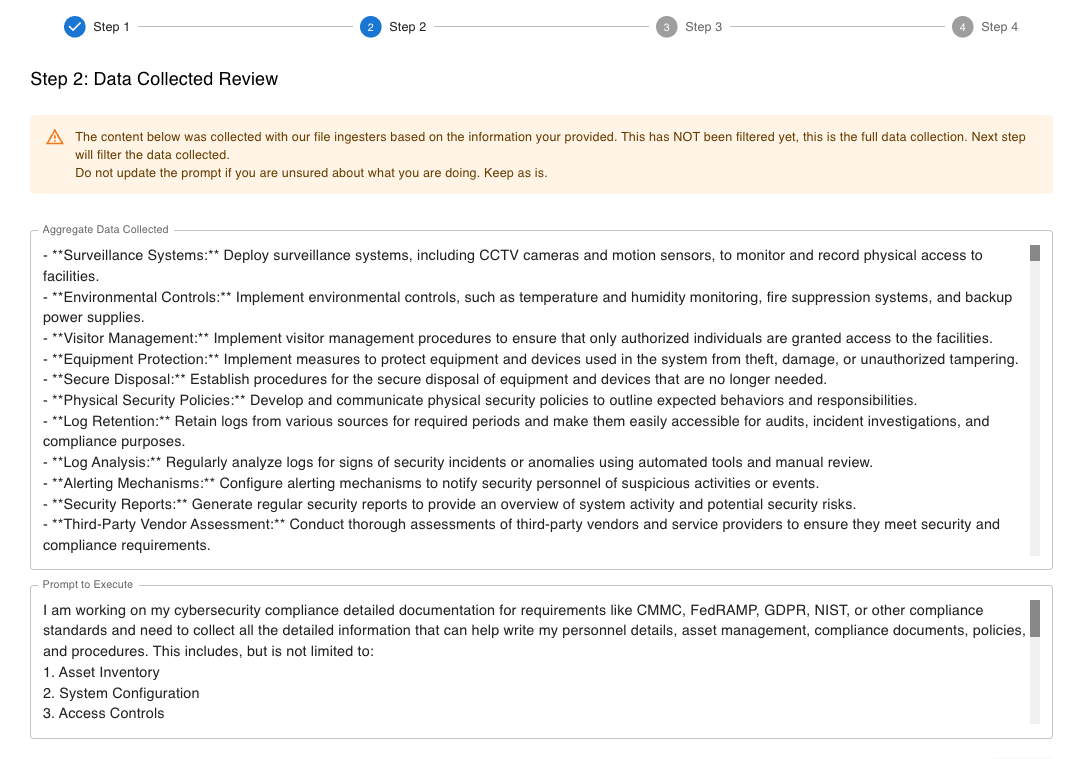
The two fields in the data collected review step are:
- Aggregate Raw Data Collected
- All the data/information provided in the data collection step will be consolidated and displayed in this field.
- No action is required in this field.
- Prompt to execute
- This field is automatically populated with a prompt, but can be edited by the user. However, it is recommended to keep the prompt as is if the user is not familiar with prompt engineering or reach out to the Ask Sage team for assistance. The purpose of this prompt is to tailor the provided content about your system.
Prefilled Prompt:
I am working on my cybersecurity compliance detailed documentation for requirements like CMMC, FedRAMP, GDPR, NIST, or other compliance standards and need to collect all the detailed information that can help write my personnel details, asset management, compliance documents, policies, and procedures. This includes, but is not limited to:
- Asset Inventory
- System Configuration
- Access Controls
- Incident Response
- Risk Assessment
- Security Awareness and Training
- Security Policies and Procedures
- Security Monitoring and Logging
- Physical Security
- Third-Party Management
- Compliance Documentation
Avoid summarizing the content or including introductory or conclusion paragraphs. Instead, extract all relevant information from the sentences provided, retaining the entire sentence if it contains any relevant information.
ACTION: Extract from this content:
Do not edit the prompt. Unless you are familiar with how the system works, it is recommended to keep the prompt as is.
Step 3. Filtered Data Content Review
On this step, the content was extracted and filtered by Ask Sage to remove unnecessary information, based on the information your provided and the prompt. Now a final review is required to remove any duplicated information in the context.
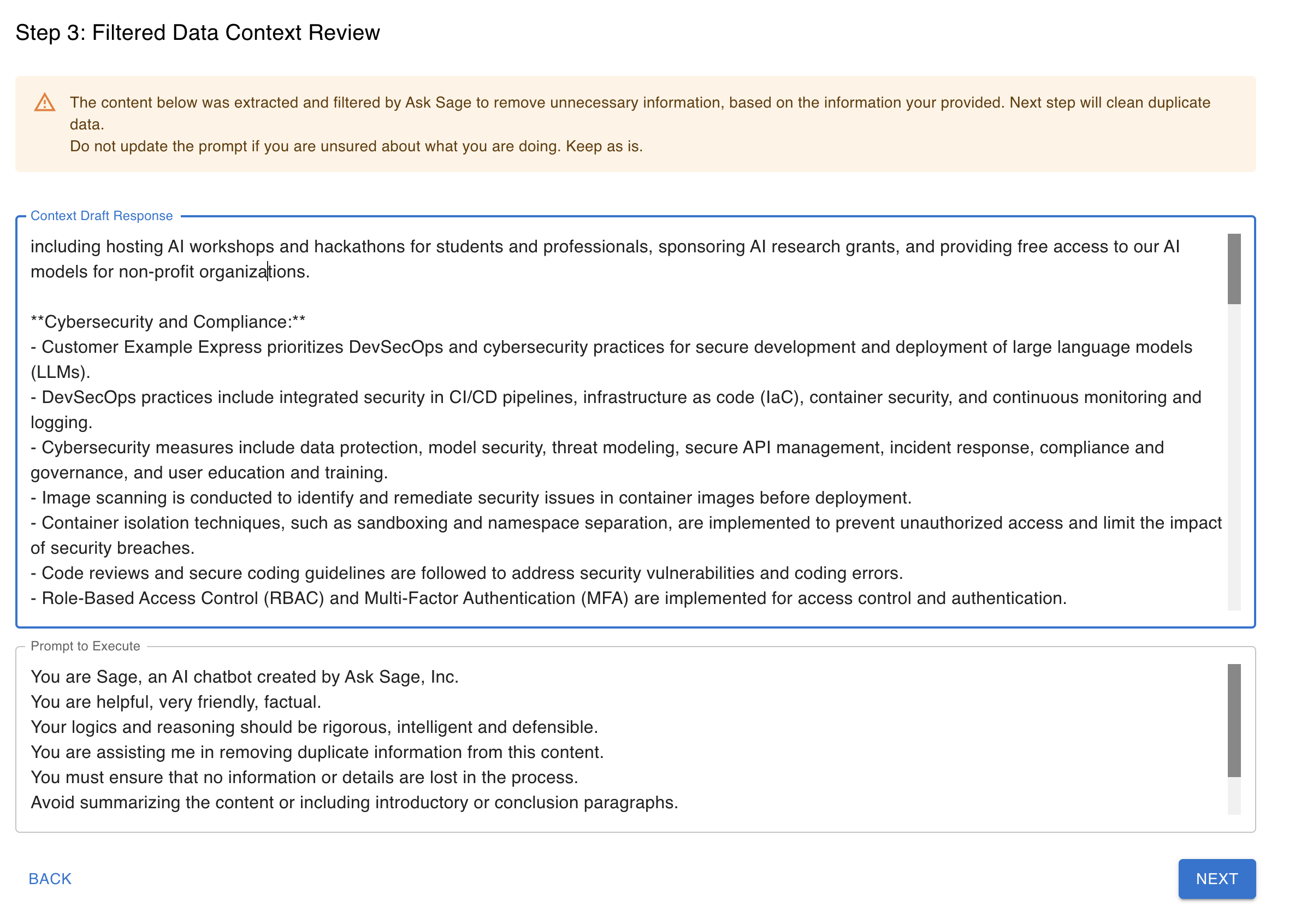
The two fields in the filtered data content review step are:
-
Context Draft Response
- The content extracted and filtered by Ask Sage will be displayed in this field. No action is required in this field.
-
Prompt to execute
- This field is automatically populated with a prompt, but can be edited by the user. However, it is recommended to keep the prompt as is because the objective at this stage is to remove any duplicated information in the context.
Prefilled Prompt:
You are Sage, an AI chatbot created by Ask Sage, Inc. You are helpful, very friendly, factual. Your logics and reasoning should be rigorous, intelligent and defensible. You are assisting me in removing duplicate information from this content. You must ensure that no information or details are lost in the process. Avoid summarizing the content or including introductory or conclusion paragraphs. Do not rephrase the content, keep the sentences as is, only remove duplicate information. It’s crucial that all information is preserved, with only duplicate data being removed from this content:
Step 4. Clean Data Review.
On this step, the content was reviewed and cleaned by Ask Sage to remove any duplicated information in the context. Now a final review is required by the user to ensure that the content is accurate, relevant and not missing any information.
This is the final step in the Manage Context section. Users will be required to review the content extracted and cleaned by Ask Sage. The content will be displayed in the Clean Data Review step. It is important to review the content and ensure that it is accurate, relevant, and not missing any information.
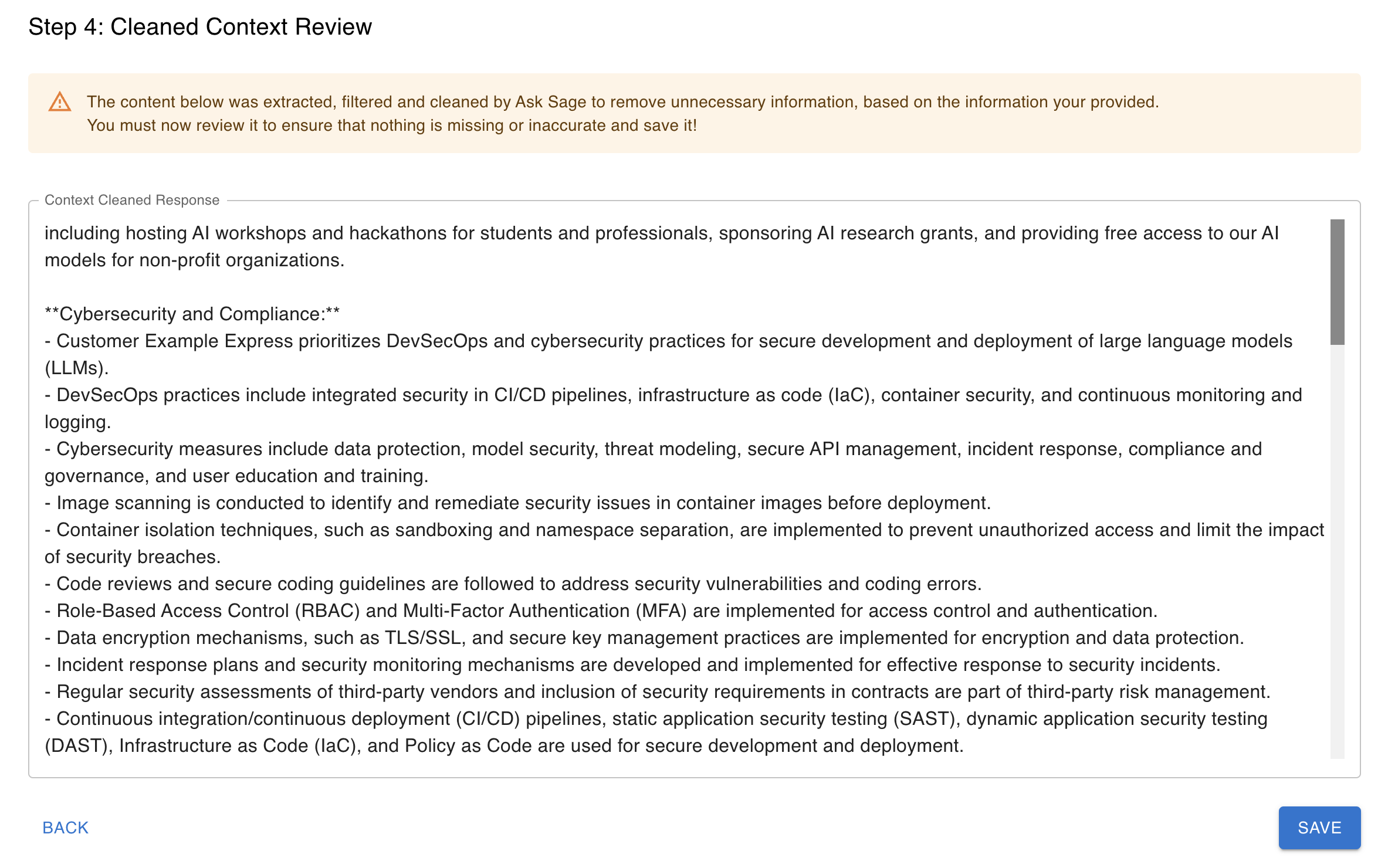
After reviewing the cleaned data response content, click on the Save button, which will save the context for the System.
Conclusion
Now that you have learned how to add a system, you can can navigate to Generate Package section. Remember to provide all relevant information about the system and ingest relevant files to train In A Box. This will help you generate documents that are relevant to the system. If you have any questions or need assistance, feel free to reach out to the Ask Sage team.
You can always go back edit details, update information and delete system as needed.
Now, let’s move on to the next section which is Generating Packages and Documents to generate documents.